By Rajvi Khanjan Shroff
An Introduction
If you are reading this, then you are currently interacting in the CyberWorld. And with the prevalence of technology, IoT, and advancements in how people connect with each other, our world has virtually expanded. In this digital age, electronic devices are an integral part of our daily lives, from getting transportation to ordering a meal. But this connection and convenience comes with a cost.
Increasingly, cybersecurity is becoming a major issue and learning to protect ourselves in the online world is a matter of utmost importance. After all, when you are online, you are on a vulnerable platform: the internet.
So, how are we protected? And what can we do to keep our information safe? And what do the terms “Cybersecurity and Information Security” mean anyway?
Ready to find out? Read on!

(Credit: Wallpaper Flare)
In Brief
The need to keep our information and belongings secure is as old as time. Essentially, cybersecurity aims to keep your information secure so only you and only people you allow can access it; information security is simply a synonym for cybersecurity. Simply put, you wouldn’t want your private information to fall into the hands of people who you wouldn’t want to give it to. This is known as confidentiality -- the idea that you can control who gets access, and who doesn’t. In real life, integrity is synonymous with reliability, and that is what it means in the context of cybersecurity as well -- the notion that data will remain safe and secure. You also want to ensure that you remain the “master” of your information so that you have control over it, and can check your information at any time. This is known as availability -- information is accessible to those with permission. Together, these make up the CIA Triad, the information model which captures a snapshot of cybersecurity and its aims.
So, how is your information, such as credit card numbers, passwords, and emails and other personal communication, kept secure on the internet?
How Your Information is Kept Secure
Cryptography, which deals with breaking and creating codes, is responsible for keeping our communication and information on the internet secure. It all comes down to Encryption, or the scrambling of text to keep intruders away. Decryption is the opposite -- it is the unscrambling of the message. To scramble and unscramble a message, a key is used.

Cybersecurity about lock and keys (Credit: Wikimedia Commons)
This might seem overwhelming to understand at first, but not to worry! Simply think of it like this: you need to send a secret message to your friend, and you don’t want anyone to know. Let’s say you are sending the word “secret” to your friend. Well, you might say, “Alright, I can make A stand for X, B stand for Y, and so on, and convert my message into this format.”
And, without knowing it, you would be performing encryption -- your message would be an example of a type of cipher called a Caesar Cipher!
It is one of the most popular examples of encryption and was developed by Julius Caesar, a Roman Emperor, to communicate with his military in secret and ensure that no prying eyes would be able to discover his plans. Essentially, you substituted every letter in the message with another letter by shifting the letters down a certain value. The Caesar Cipher is an example of an encryption algorithm, a procedure used to transform a plaintext (the regular message) to the Ciphertext (the encrypted message).
In your situation, to send a message of “secret,” you first decided on the shift you would put onto each of your messages, and then created a “new” alphabet, called a cipher alphabet. According to how you changed your letters, there was a shift of 3 (because if you made an “A” now equal an “X”, you had to shift the “A” three units down). This means that our generated ciphertext is now “vhfuhw.” For your friend to decrypt it, she would simply shift the letters to the right by 3 (the key, or the password to unlock the message, in this case, is 3) to get the word “secret.”
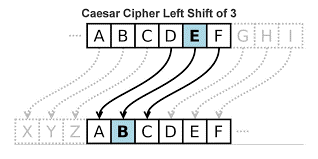
A diagram of the Caesar cipher (credit: Secplicity)
Now, the Caesar Cipher is a quite straightforward algorithm, making it easy to break. Imagine that Eve wanted to eavesdrop on your conversation. If you had sent your friend that message over the Web, Eve could have intercepted the ciphertext and easily discovered the message. This is why, as civilization advanced, more complicated algorithms which were harder to crack arose. For instance, the Vigenère cipher (a famous cipher in use for about 300 years, created by a French cryptographer Blaise de Vigenère and cracked by Charles Babbage, an English polymath) uses different Caesar shifts at different points to encode a message, and a substitution cipher substitutes every plaintext character for a different ciphertext character (it’s not like a Caesar Cipher because the cipher alphabet is completely jumbled, and not just shifted down). As computers evolved and came into ubiquitous use, there arose a need for the “coders” to outsmart both the computing power and skills of the “breakers” or hackers. They did so by employing encryption algorithms that are too hard to crack given the limitations of modern technology.
So, what are some encryption algorithms in use today?
The most common ones include RSA, AES, Triple DES, and Blowfish.
RSA: Standard, quite a safe method for encrypting data and transmitting it across the web; This algorithm is an asymmetric encryption (which is also known as public-key cryptography), which means that two keys are used in the encryption process -- one that is private and the other public. Both of these are used in such a way that it has more strength than symmetric encryption, which uses only one key.
AES: Considered to be extremely strong, this method is used by the U.S. government to protect classified information and is implemented in software to encrypt sensitive data
Triple DES: Although it is almost outdated now, it was once the most popular symmetric key encryption algorithm. It was mainly used in the financial industry.
Blowfish: A symmetric key algorithm that is a popular choice today as it is fast and effective. Its main usage is in e-commerce, to ensure safe payments and in password management apps and tools.
Now that we have learned about some techniques used to keep information secure, how are they hacked?
“Shh, someone is listening”: What are common approaches hackers use, and how can we protect ourselves?

(Credit: Wikimedia Commons)
Denial of Service/Distributed Denial of Service (DoS/DDoS): Businesses, organizations, and even governments are susceptible to hackers. One common hacking technique is to bring down the system through an overload of requests. This shuts the system down as the processing is slowed and ultimately leads to a crash.
Eavesdropping: This is when hackers “listen in” on your network, catching important information. To protect yourself, avoid going on unsecured networks (usually public.) If this is not possible, use a VPN (stands for Virtual Private network; think of it as a “secret tunnel” in a public network that helps keep your internet traffic, such as your searches and any information you send over the internet, anonymous) when connecting to public wifi.
Malware: Include viruses (malicious software that replicates similar to a biological virus), Trojans (malware designed to seem innocuous), spyware (used to learn more about a person for malicious intent, such as obtaining bank account details), and much more. To protect yourself, be cautious when opening emails, disable pop-ups as they often contain malware in disguise, and only don’t download new apps from unknown sources.
Phishing: Using emails and other techniques to trick a person into giving their personal information. To protect yourself, be cautious about urgent-sounding emails and when opening links and documents from them.
A few other important tips:
Create strong passwords (12+, hard to guess, use special characters, and use different ones for different accounts -- don’t repeat!)
Make sure there is a padlock sign to the left of the web address when online shopping or entering account details, as this means that your connection is secure.
Disable unnecessary cookies. They are often used by hackers and can take up storage space in your computer anyways.
References
Contel Bradford, “5 Common Encryption Algorithms and the Unbreakables of the Future.” StorageCraft Technology Corporation, 3 Oct. 2016, blog.storagecraft.com/5-common-encryption-algorithms/.
Laliberte, Marc. “Historical Cryptography Ciphers: Secplicity - Security Simplified.” Secplicity, Secplicity, 14 July 2017, www.secplicity.org/2017/05/25/historical-cryptography-ciphers/.
Mitani, Masaaki, et al. The Manga Guide to Cryptography. Ohmsha, Ltd., 2018.
Parms, Jason. “Symmetric vs. Asymmetric Encryption – What Are Differences?” SSL2BUY Wiki - Get Solution for SSL Certificate Queries, 7 Feb. 2019, www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-what-are-differences.
SINGH, DR SIMON. CODE BOOK: The Secret History of Codes and Code -Breaking. FOURTH ESTATE LTD, 2011.

تعليقات